Can Clicking a Link Get You Hacked?
How much damage can a malicious actor do by getting someone to click on a link? This blog focuses on exploring the different vectors of attack, across a number of browsers, to establish whether clicking a link is enough to result in compromise of a computer, and to further explore how severe the compromise can be.
Avoiding downloading and opening files we don’t trust is a great way to minimize the likelihood of getting compromised, but what about visiting a website? Can clicking a link result in getting compromised by a malicious actor?
Safari, The Browser That Automatically Opens Files
We’ll start with a feature that seems to be geared towards improved user experience but introduces a vector for an attack using files to deploy malware. Safari has a built in feature that is enabled by default, and automatically opens files which it downloads that are considered to be “safe”.
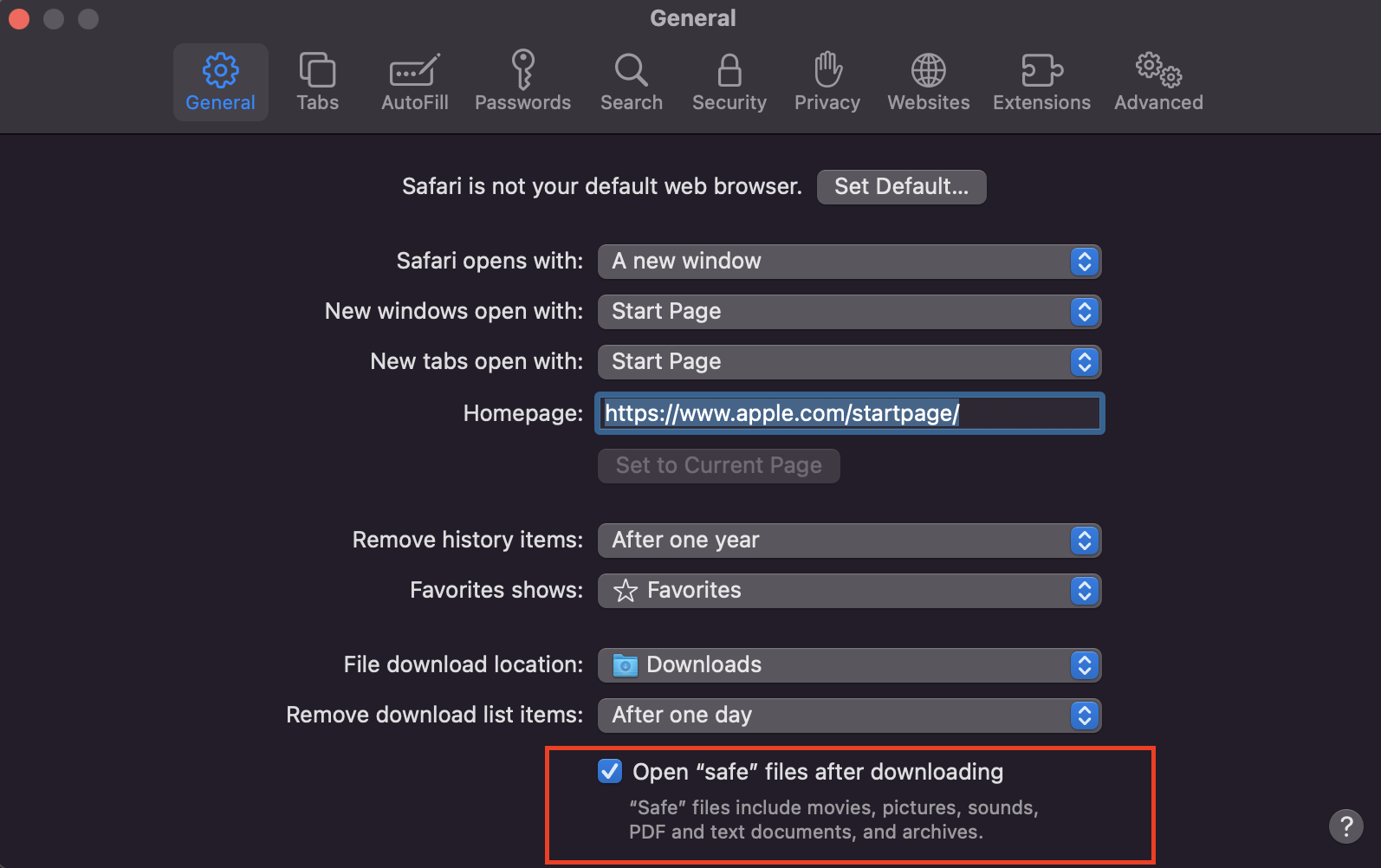
The question is: how does Safari determine what a safe file is? Detecting a malicious file is not trivial, because new methods of concealing malware inside of files is emerging continually - this means that, at best, the method Safari uses to figure out whether a file contains malware captures the known methods of concealing malware in files. The likelihood that it is able to detect all malicious files disguised as pdfs, images, videos and other media considered “safe”, is extremely low. Thus we encounter the first example of how clicking a link can result in computer compromise, and in this case a full system compromise, as the file is not being opened within the sandbox of the browser, it is being run on the host operating system, drastically increasing the likelihood of a complete compromise with arbitrary code execution capabilities which opens doors to a large number of attacks.
To focus in on one file type, pdf, it’s easy to see why it would be difficult to distinguish if a file is secure or not. There are 2000+ known pdf related CVEs as of writing of this article. New ones are being discovered each year, and this is largely due to the complexity of the pdf file format.
One of the media listed is “archives”, which is another example of something that can hide malware inside of it. An archive in and of itself is not malicious, decompressing it will not cause issues in most cases, but the files that are inside of the archive could, and the fact that Safari automatically decompresses things may make the user feel that opening the files contained within is not a significant risk. In 2006, Apple changed the way “auto opening” works on compressed data, as it used to automatically open the contents of the archive, but that’s no longer the case. The reason they changed the way the feature work is because malicious actors packed scripts inside of the archive, which installed malware on the target’s machine.
Breaking the Sandbox
One of the primary tenets of browser security is the idea that a browser should be sandboxed. Sandboxing is the practice of isolating programs in order to reduce the blast radius in the case of a vulnerability.
One would hope that vulnerabilities which allow escaping the sandbox aren’t that frequent or at least don’t have major impact on a system, but they are actually relatively common and often allow the attacker to perform arbitrary code execution on the system.
In 2022, so far there seem to be 10 sandbox escape vulnerabilities with Google Chrome browser. These vulnerabilities are patched quickly but the users aren’t always quick to update their systems, which means a large amount of users are likely to be impacted by these vulnerabilities.
Why does this happen? Again, as in the case of pdf files, the increased complexity of code such as that of the V8 JavaScript engine, which powers most modern browsers, renders it nearly impossible to fully secure. The amount of code and all the possible ways it can run creates a “state space” so large that it’s not practical to ensure that all undesirable states in the system are eliminated.
Summary
The conclusion is that, yes, just clicking a link can result in your system being compromised, and it’s largely due to the fact that the software that runs the modern internet is increasingly complex, and as a result, more difficult to secure. To protect ourselves we can do a few things:
- Disable javascript in our browser. This can reduce usability of certain websites but drastically reduces the surface area for sandbox escape exploits.
- Stick to trusted websites. If you are delving into less frequently explored parts of the internet, you are a lot more likely to land on a website that has malicious intent. Keep an eye out for malicious links that you may be sent via email or other channels.