I Have a Password System
Even though passwords are one of the most common and basic types of security mechanisms, few understand what makes a good password and how to deal with password management. I frequently come across individuals who have a “password system” they came up with. Usually they don’t reveal how it works exactly, but they proudly profess that they don’t need to remember all their passwords because they “modify” their main password based on the service it’s used for. Although to many this seems like a good practice, it is unfortunately a recipe for disaster, and the intuition as to why this doesn’t work isn’t immediately obvious. It’s better than using the same password verbatim, but not by a lot.
One of the most common attacks used by threat actors is called “credential stuffing”. Credential stuffing consists of a threat actor using a set of credentials from one service, to try to break into another. For example, in 2016, LinkedIn had a data breach that leaked ~160 million passwords. Threat actors got a hold of these passwords, and then started methodically testing out these credentials against different services. The work smarter, not harder principle is embraced by threat actors, and they are able to automate this process so that they can simultaneously try to break into many different services, with many different leaked credentials. For individuals who use the same password everywhere, and no 2FA (Two Factor Authentication), their accounts are broken into almost immediately. Those who use a “system” to build their passwords buy more time for themselves, but they are not immune. If a threat actor is motivated to compromise an individual, they can spend time and resources on trying to figure out the “system” or the pattern used to build a password by a user, or obtain breach data from multiple services, and then compare the passwords across different data breaches, to figure out what pattern the individual uses to construct their passwords. Password cracking is an extremely sophisticated category of attacks so don’t underestimate their capabilities. There are good news though, you can avoid password issues by following a few simple guidelines. These guidelines may add a little bit of friction for you, but they will also add magnitudes of order more friction for the attacker.
1. Use a password manager.
A password manager allows you to store passwords that are long, complex and unique, and never reused without having to worry about remembering them. Come up with a strong password to protect access to your laptop and password manager, and generate the rest of your passwords using a built-in password generator - they can be as long as the services allow them to be. They should be at least 16 characters long, but you should aim for something longer, for example 42 characters. There are a number of great password managers available so choose one and use it!
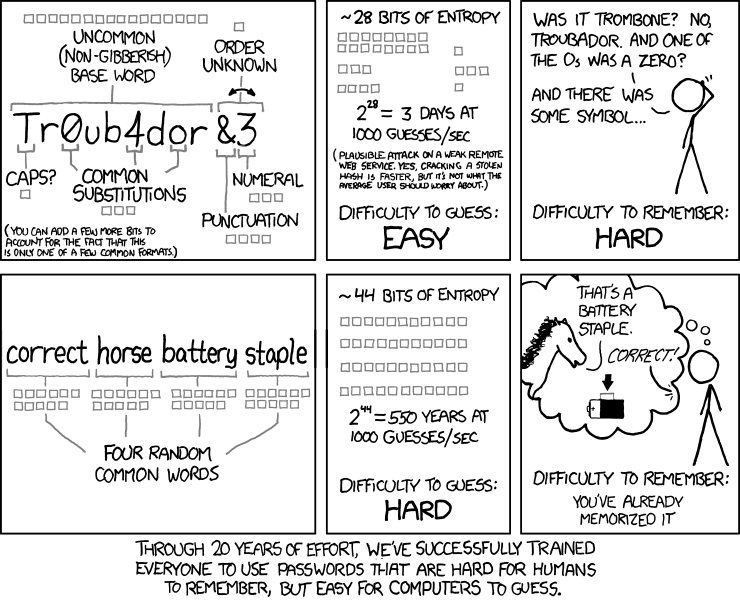
2. Learn to create strong passwords.
The few passwords that you do have to remember should be long, complex and unique. One easy way to achieve this while making the password memorable is using words interspersed with special characters and numbers. For example, a strong password might look like this “GHOul$$meager757-SyLLa^bus” (don’t use this password, come up with your own). The idea is that your passwords should not contain any information that someone could guess about you, well known phrases, or any other information that can be guessed. Think of random words, and then glue them together using symbols and numbers, re-arrange words, intersperse symbols between letters and so on - you get the idea.
3. Use 2FA/MFA
More on the merits of 2FA/MFA (Two Factor Authentication / Multi Factor Authentication) coming soon, but suffice to say you should always use some form of 2FA.